Matchless Which Is A Non Technical Type Of Attack Technique

Patch for fixing the problem is released.
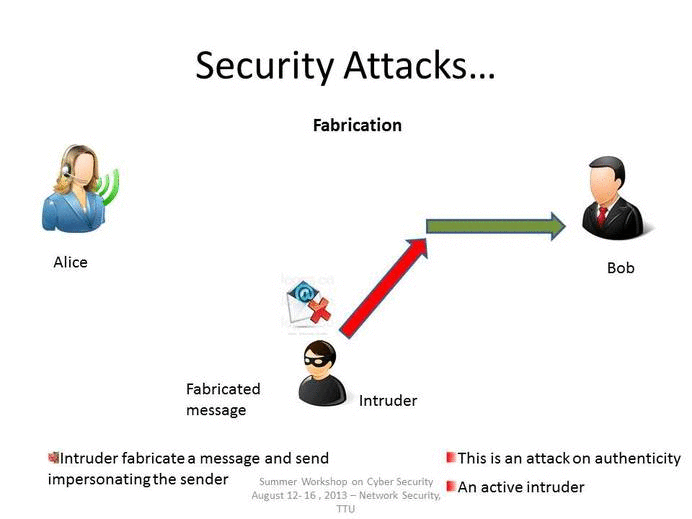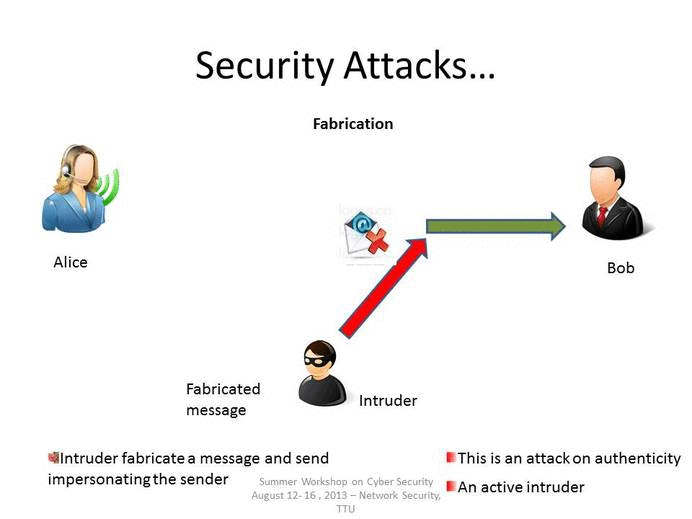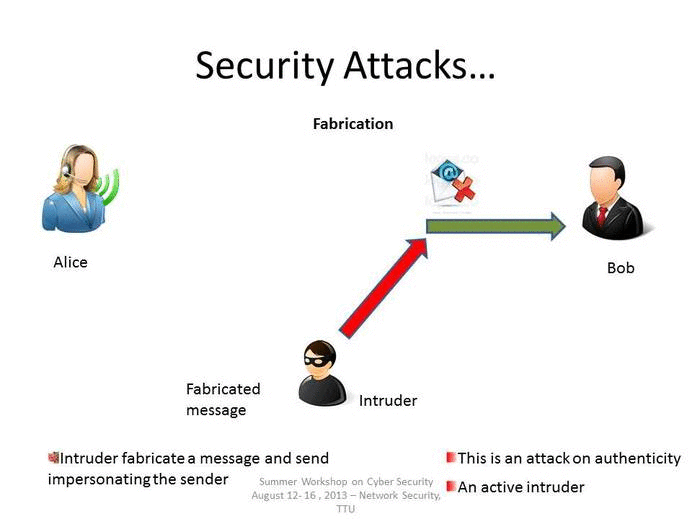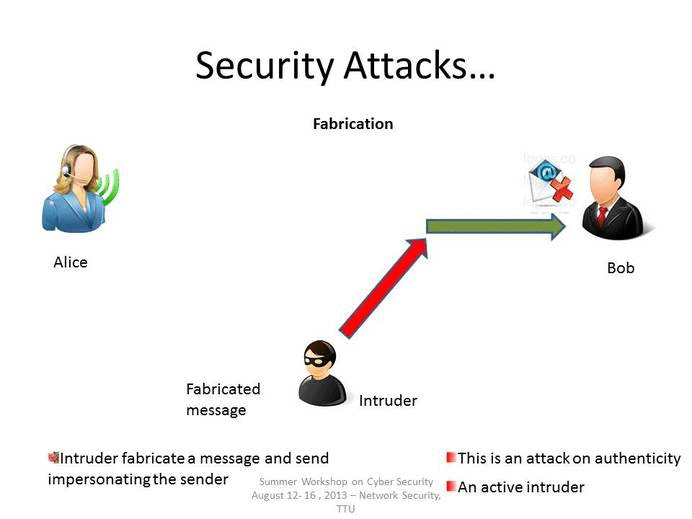
Which is a non technical type of attack technique. Any technology implemented improperly can create a. Which of the following is a non-technical type of intrusion or attack technique. Up to 20 cash back Social engineering describes a range of non-technical attack techniques that are used by cybercriminals to manipulate users into over-riding security or other business process protocols performing harmful actions or giving up sensitive information.
Computer Forensics is the application of investigation and analysis techniques to gather and preserve evidence from a particular computing device in a way that is suitable for presentation in a court. Criminals use social engineering tactics because it is comparatively easier that other attacks. Other non-technical social engineering techniques includes role playing baiting breaking in and tailgating.
It is a term that describes a non-technical attack that relies on human interaction and tricking people to break normal security procedures. Which of the following is not an example of non-technical attack techniques. It involves tricking target users to.
This is a type of attack that is commonly referred to as a denial of service but the actual technique is a saturation technique. In the non-technical type of attacks it is not required to have. Physical attack methods include.
Which of the following is not an example of non-technical attack techniques. Which of them is an example of grabbing email information. Social engineering is the art of interacting with people either face to face or over the telephone and getting them to.
-It is a type of malicious code or software that looks genuine. An attack between the time a new software vulnerability is discovered and the time a. Which of the following is not an example of non-technical attack techniques.